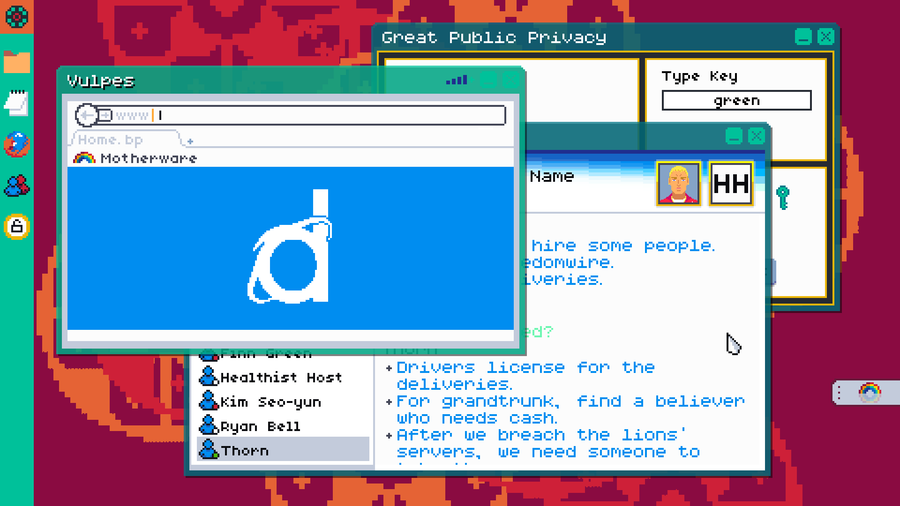
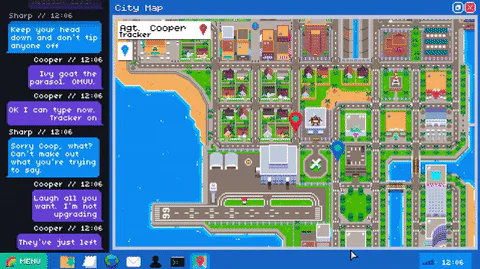
Part of MI7’s Mainline software allows operatives to “take control” of suspects computers. During this process players will encounter operating systems such as Rainbows, Cherry and Peyotex (all inspired by the great OSs of 2010). Of course, these won’t be clean installs. Players will be free to interrogate their target’s computers, filled documents, programs, secrets and hopefully the evidence needed to secure a conviction.
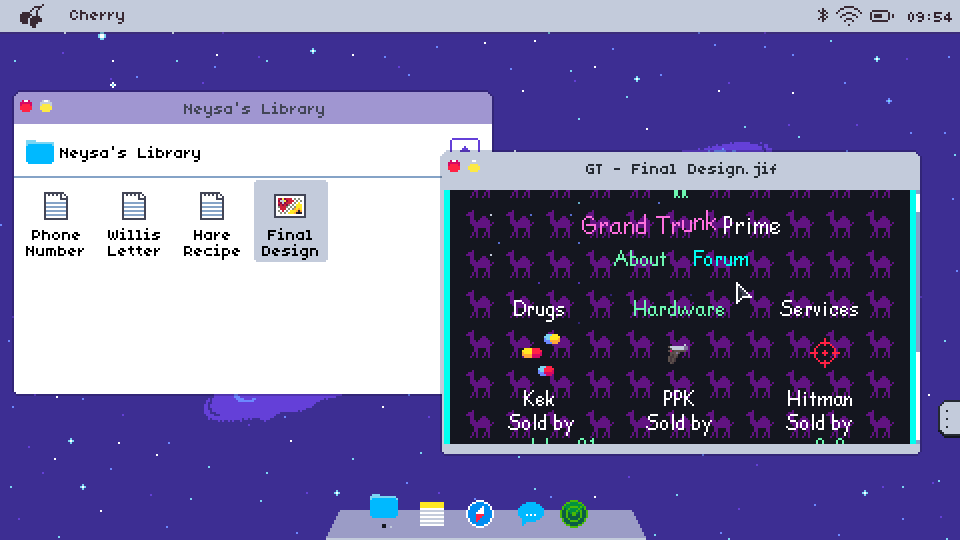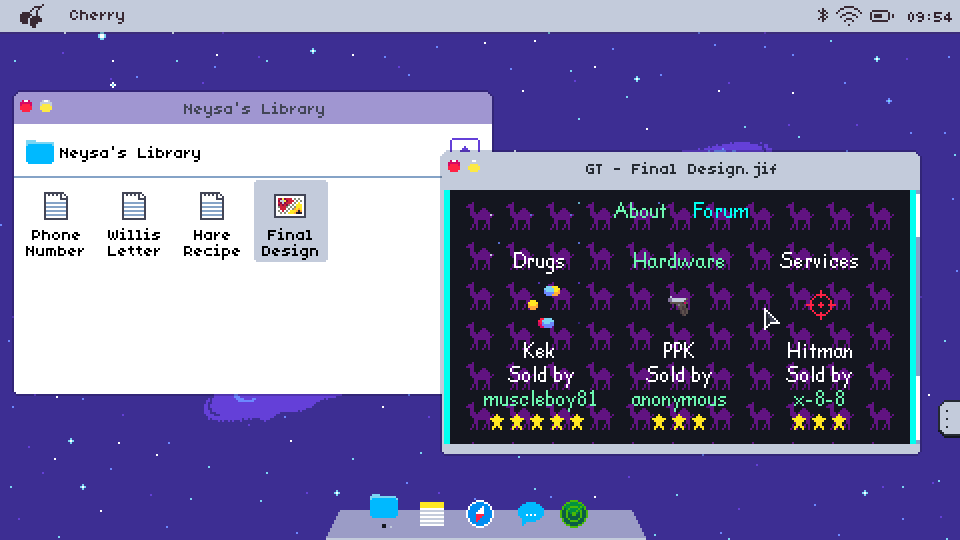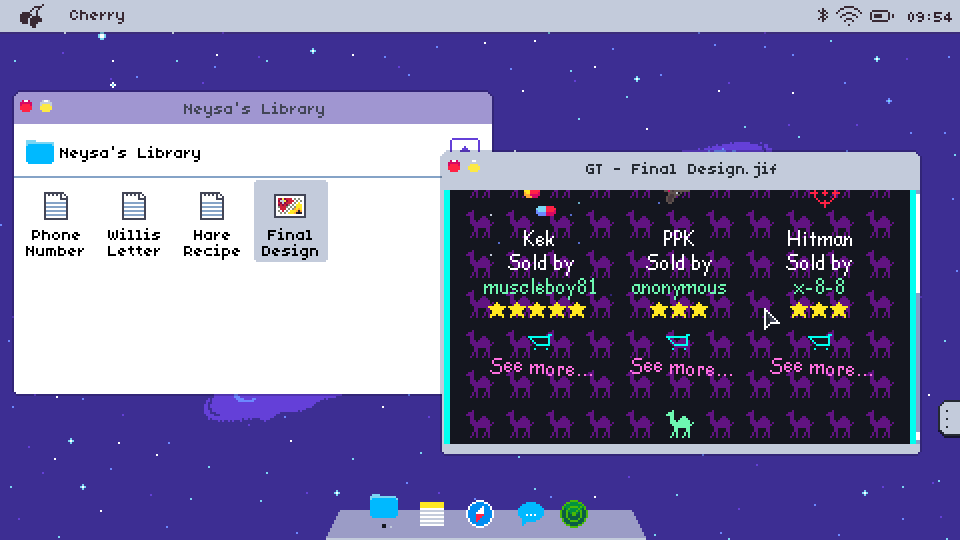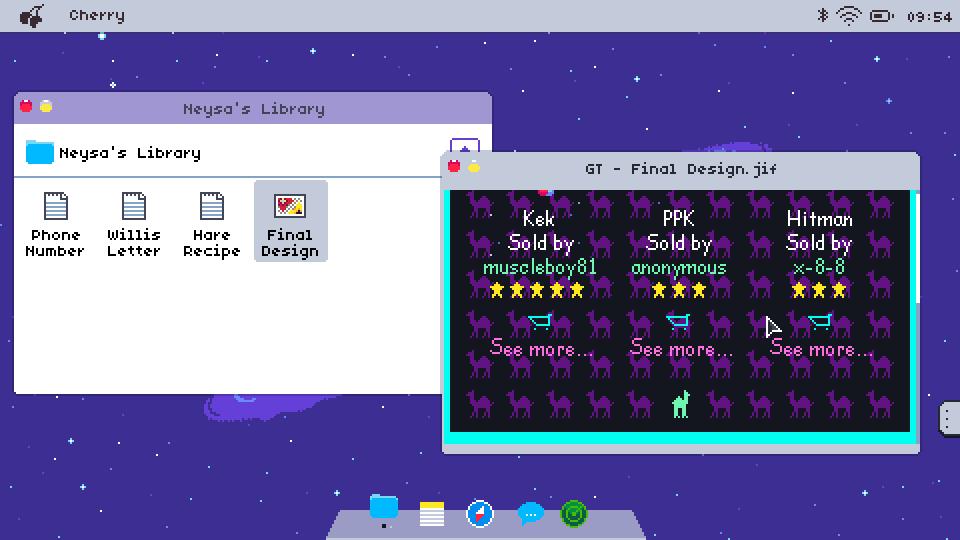
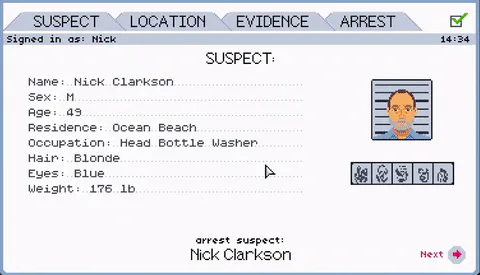
Naturally, suspects can be very wary. At best, files discovered may be encrypted or, at worst, be hidden on remote servers. Operatives will need to employ new programs, which usually come with the operating systems, to gather the evidence needed to instigate an arrest.
Alternative operating systems can hide plenty of secrets, a fact not helped by the shady nature of their owners. Operatives will need to be mindful that they are following a bona fide trail and not following red herrings on a wild goose-chase. Attention to detail and thoroughness are qualities that will be needed always - the perpetrators aren’t going to make things easy and they certainly don’t have any plans on being caught.







2 comments